A vulnerability scanner detected that the EventSentry collector is using a weak cipher, how can I resolve this?
When you scan the collector with a vulnerability scanner, it will list all ciphers that are currently supported by the Windows OS. However, the only cipher that will be used by the collector is the cipher used in the collector certificate. You can check what cipher the collector cert is using with openssl.
openssl s_client -connect COLLECTOR_IP:5001
Replacing "collector_IP" with the IP of your EventSentry server.
This command will reveal if the collector is using a strong cipher, and if Secure Renegotiation is supported. Secure Renegotiation should be OFF, so if a client asks to downgrade to RC4 it will be denied.
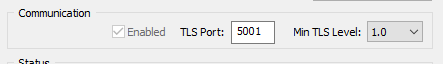
If you open the EventSentry console to Home > Collector, you can also adjust what TLS versions the collector will allow. Setting the "Min TLS Level" setting to 1.0 means your agents could connect with TLS 1.0, but your agents will still connect to the collector with the strongest TLS version available up to 1.3.
If you set the "Min TLS Level" setting to 1.2 or 1.3, make sure all of your agent hosts support this TLS version. If you do make any changes, follow these steps to make sure all your agents and collector know to use this new protocol:
1) Click Home > Save (dropdown) > Save and deploy if this is an option, otherwise just click Home > Save.
2) Click Groups > Push Configuration > Go
3) Click Groups > Manage (dropdown) > Restart Agents > Go.
4) Finally click Home > Services and restart each service here.
After this, open Web Reports to Settings > Collector Status > Connections tab and refresh this page a few times to make sure all your agents can reconnect successfully.
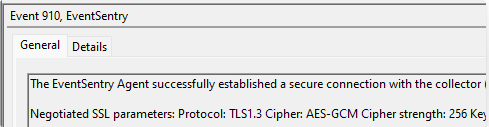
Lastly, if you like you can force the collector to only use certain ciphers. First, check what TLS version your agents use to connect to your collector. You can see this in the 910 event in the application event logs that generate when the agents make a connection. This is also how you can see the cipher it uses:
With TLS 1.3 there are only three ciphers that are supported by default:
TLS_AES_256_GCM_SHA384
TLS_CHACHA20_POLY1305_SHA256
TLS_AES_128_GCM_SHA256
With TLS 1.2, you can manually set the ciphers that the collector supports.
- Open the registry editor on your EventSentry server
- Navigate to the Registry key:
HKEY_LOCAL_MACHINE\SOFTWARE\netikus.net\EventSentry\Collector
- Create a String Value (REG_SZ), named:
secure_publickey_supported_ciphers
Then you can edit the value and paste the ciphers you wish to support, separated with a semicolon with no space. So for example:
TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384;TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256;TLS_ECDHE_ECDSA_WITH_AES_256_GCM_SHA384;TLS_ECDHE_ECDSA_WITH_AES_128_GCM_SHA256;TLS_RSA_WITH_AES_256_GCM_SHA384;TLS_RSA_WITH_AES_128_GCM_SHA256;TLS_DHE_RSA_WITH_AES_256_GCM_SHA384;TLS_DHE_RSA_WITH_AES_128_GCM_SHA256
If your security scanner prints that Diffie-Hellman is of insufficient strength (Key size <2048), you can disable the use of DHE and use only ECDHE by setting these ciphers as the registry key:
TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384;TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256;TLS_ECDHE_ECDSA_WITH_AES_256_GCM_SHA384;TLS_ECDHE_ECDSA_WITH_AES_128_GCM_SHA256;TLS_RSA_WITH_AES_256_GCM_SHA384;TLS_RSA_WITH_AES_128_GCM_SHA256
Remember that the TLS version needs to be set to v1.2 in the collector page of the EventSentry console.
After setting the ciphers in the registry, open services.msc and restart the EventSentry Collector service. This will force the collector to only use the ciphers you set.
Note: You can also check the minimum TLS version that is accepted on a port via the Powershell script that available in our GitHub repository HERE