Detect Ransomware Patterns
When every second counts
Stay ahead of what is happening with your sensitive information and fix problems before they start.
How EventSentry detects Ransomware
Unlike other security solutions which rely on static rules and known signatures, EventSentry detects ransomware by analyzing activity from multiple vantage points.
By leveraging advanced security algorithms specifically designed to detect malware, EventSentry can detect Ransomware and similar attacks in real time - whether it’s at the reconnaissance, exploitation, persistence, propagation or execution stage.
By automating over 200 system security checks, EventSentry also helps reduce the attack surface to make a Ransomware attack less likely to succeed in the first place.
EventSentry also enables forensic analysis by maintaining a full audit trail of all system activity.
Potentially compromised endpoints can be contained and blocked in a variety of ways to limit the scope of an attack.
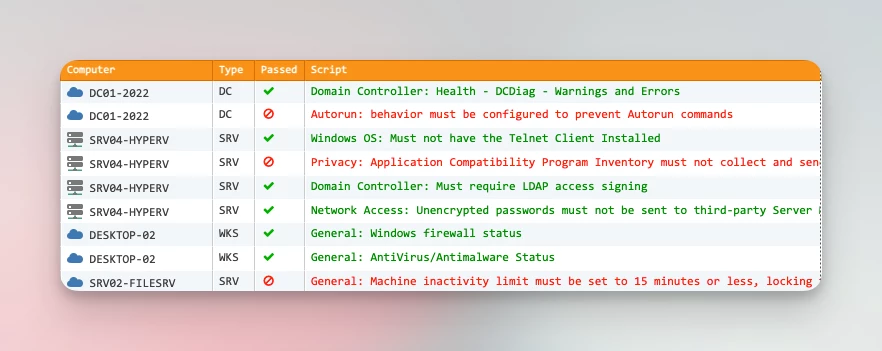
Continuous analysis of attack surface on all end points
With over 200 validation scripts at its disposal, EventSentry continuously checks critical system settings to make sure all monitored endpoints follow best security practices such as MITRE & NIST. The result is a reduced attack surface will also facilitating compliance requirements.
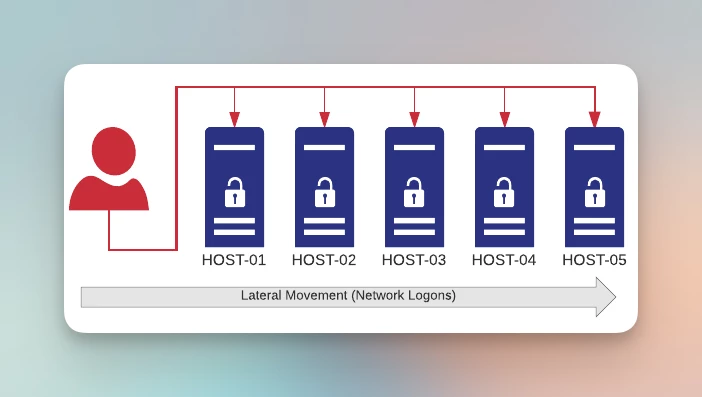
Lateral Movement Detection
Often used to spread from an infected endpoint inside the network, logons (e.g. SMB, RDP) or processes moving laterally can be detected by EventSentry.
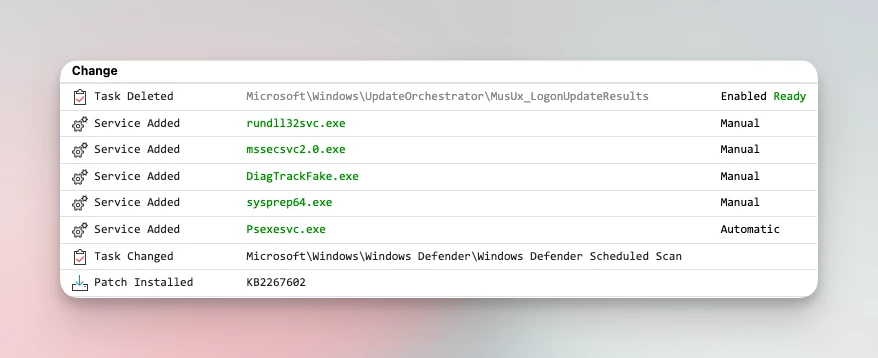
Detect system changes
Malware often uses services, drivers and scheduled tasks for persistence. Through its extensive system inventory capabilities, EventSentry detects changes to services, drivers, scheduled tasks, system files (FIM), installed software - even browser extensions.
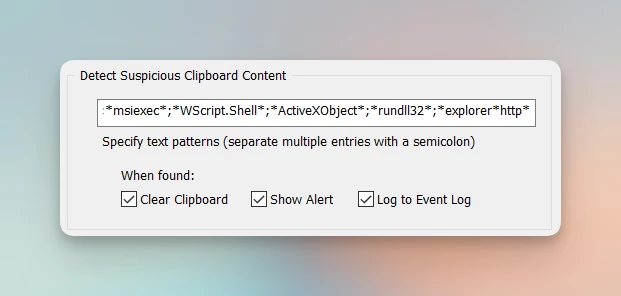
Clipboard Monitoring
Some malware variants trick end users into executing malicious commands by polluting the clipboard. EventSentry can detect, erase and alert on malicious clipboard content.
Execute corrective actions
After detection, EventSentry can perform corrective actions such as disabling network shares, rebooting or performing a custom action.
Detect unusual file access frequency and CPU usage
Ransomware attacks often cause unusual performance patterns and can be detected with EventSentry’s performance and event log monitoring.

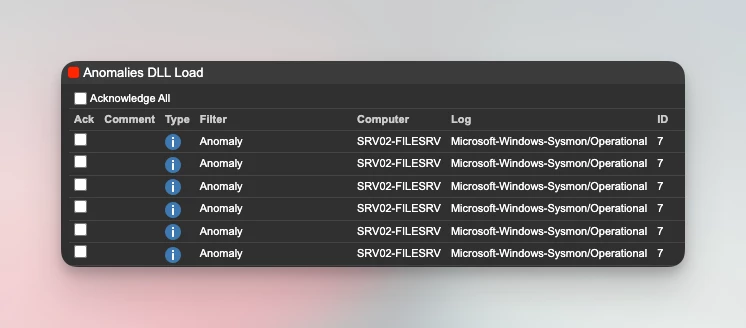
Detect new DLLs loaded with Sysmon
DLL-sideloading - a popular technique to infect systems and avoid detection - can be identified with Sysmon and anomaly detection.
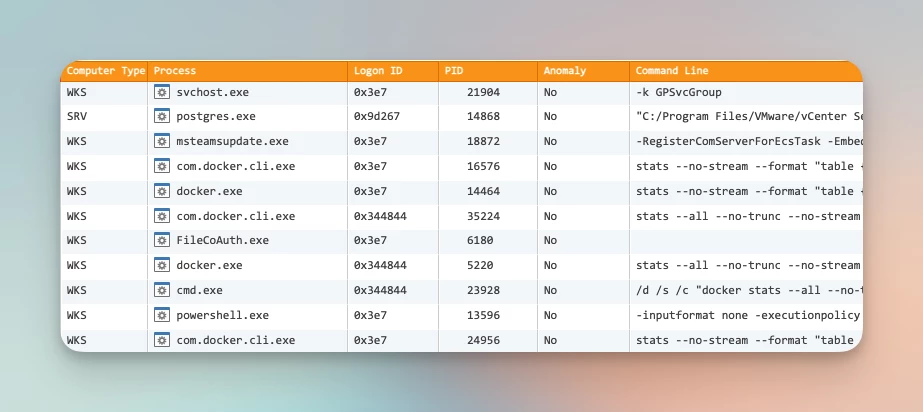
Detect New Processes
Never-before seen processes can be identified by path or file checksums with anomaly detection.
Process Masquerading
Malware often uses common process names (e.g. svchost.exe) to hide in plain sight. EventSentry’s spoof detection feature identifies these malicious processes.

Detecting New File Extensions
Ransomware often uses unique file extensions when creating README files and encrypting data. EventSentry can create a baseline of all known file extensions and alert on new file extensions being discovered on the network with anomaly detection.

Monitor your servers and critical data
Take control of your security, compliance, and operational stability with real-time monitoring. Safeguard your business against threats, ensure regulatory compliance, and maintain the seamless operation of your IT infrastructure.
Start Monitoring Now!
Protect your business with a proactive server monitoring.
What does EventSentry offer?
Log Monitoring
Real-time event log monitoring and remediation.
Validation Scripts
Evaluate security settings across your Windows servers.
Dashboards
Help you keep an eye on key performance indicators.
Compliance
Built-in dashboards with detailed reporting.
Real-time Alerts
Immediately trigger alerts and corrective actions.
Active Directory
Search object changes down to the attribute level.
Performance
Quickly spot unusual activity on your network.
Change Detection
Identify unexpected changes the moment they occur.
Keep your data secure
On-premise or Bring Your Own Cloud (BYOC)
Easy Deployment
Built-in Compliance
We predefine compliance rules and dashboards.
Automated updates
Keep your agents up to date with the latest configuration.
Streamlined communication
Triggered actions are compressed and encrypted.
Getting started with EventSentry is easy
-
Start an evaluation
FREE fully functional for 30-days
-
Install EventSentry
Quick installation / Monitor in minutes
-
Centralize audit logs
Built-in dashboards / reports
Powerful and flexible SIEM solution
Whether you are meeting a compliance requirement or simply being proactive, EventSentry's unmatched functionality will bring visibility into your IT infrastructure and increase uptime.
FREE support and updates with new licenses
Validation Scripts for latest security recommendations
software version checks
Awesome