How can I be alerted when a specific process starts?
Windows generates an event ID 4688 in the Windows Security Event Log when a process gets launched. In EventSentry, an include filter that monitors for those events needs to be created and associated with an email action so that an email alert is sent once this (specific) process gets started.
Event ID 4688 Example
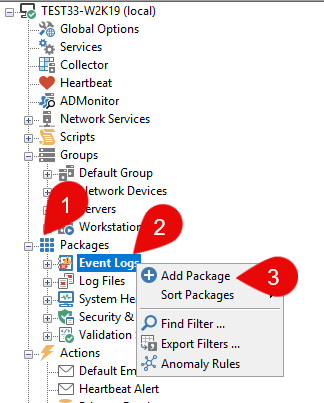
To do this, open the EventSentry Management Console and expand "Packages" (1), and then right-click on "Event Logs" (2) and select "Add Package" (3) (label this "Process Alert").
Creating a new Event Log Package
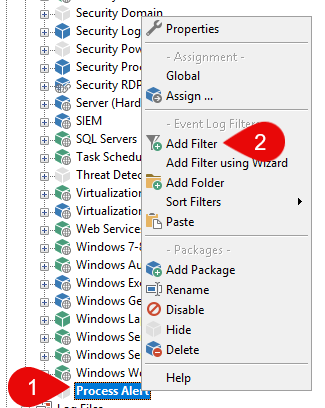
Then, right-click on the "Process Alert" package (1) and select "Add Filter" (label this "Process Alert (email)") (2).
Creating a new Filter for the just created Event Log Package
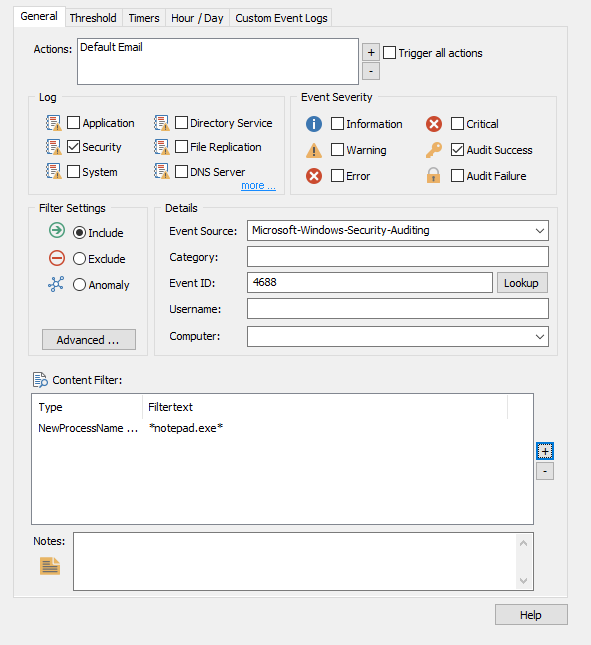
Then, click the "Process Alert (email)" filter and enter the following details:
Log: Security
Severity: Audit Success
Source: Microsoft-Windows-Security-Auditing
ID: 4688
Click the (+) next to "Actions" and add an email action to be alerted there.
Event Log Package Example
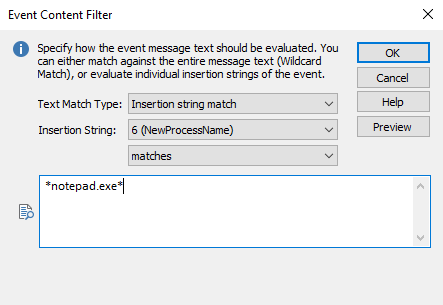
In the lower area of the general tab, add a Content Filter and sellect "Insertion string match", select #6 and type with the process name, for example:
*notepad.exe*
Note: Since the event includes the entire path of the process it's important to use a wild card character when not specifying the full path to the executable.
Content Filter
Next, right-click on the "Process Alert" package and select "Assign," and assign the package globally (all hosts) or "Assign...." (individual hosts) and click save. Once the configuration gets saved, the collector will update the configuration on the remote hosts, and when this specific process gets launched, the EventSentry agent will send an email.