Can I detect Ransomware by monitoring if a new file extension has been detected on my network?
Since Ransomware often manifests itself by creating (encrypted) files with new file extensions, detecting never-before seen file extensions can be an effective way to detect Ransomware in real-time.
EventSentry can utilize the following features to detect new file extensions in real time:
- Anomaly Detection
- Insertion String Override with Regex
To detect new file extensions, you must meet the following requirements:
- EventSentry v5.1 or later must be installed (v5.2 recommended)
- File Access Auditing (for write activity) must be enabled in Windows (event id 4663)
- Windows is set to English (other languages are supported but require a different regex than what is included in the filter below)
Please note that it is not necessary to consolidate event id 4663 to the database.
1. Enable auditing
Enable NTFS auditing for write access on all directories you wish to monitor for new extensions. If auditing was setup successfully, then you should see 4663 events in the security event log of the respective machine whenever files are added or changed in those directories. Please see our documentation for more on how to enable auditing: Link
2a. Create Anomaly Filter (Fast-Track Mode)
You have two options on how to create your filter. The first option allows you to skip steps 3 & 4 below by automatically creating the filter using JSON. To do so, first copy the JSON code from step 6 to the clipboard and simply add a new filter in your preferred package in the EventSentry console. Then, click the Apply Json Rule button in the ribbon and make sure to replace the content filter ("TESTGROUND") with your domain name. Then proceed to step Step 5.
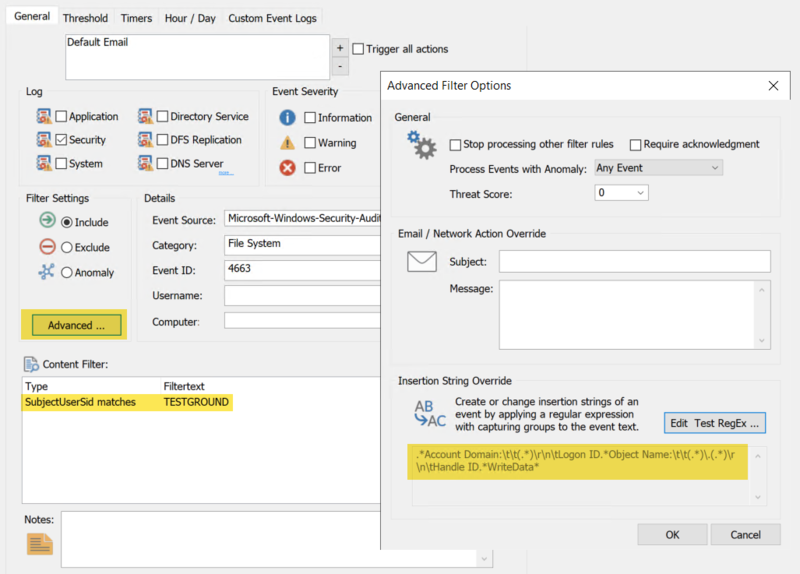
2b. Create Anomaly Filter (Manual Mode)
Alternatively, you can manually create a new include-filter that matches the key properties of a 4663 event as shown in the screenshot in step 3 below. It is important that the content filter (shown as TESTGROUND in our example) matches your domain name. The description of the insertion string (SubjectUserSid) can be ignored, since we will overwrite insertion strings with a regex pattern.
Adding your domain name as a content filter is important, as it will ensure that the filter will only match if the regex is successfully parsing the event. For example, events resulting from a folder change will be ignored.
3. Setup Regex
Once the base properties of the filter are setup, the regex pattern which extracts the file extension needs to applied to the filter. Click the Advanced button and Edit Test RegEx. In the resulting dialog, enter the following regular expression:
1 |
.*Account Domain:\t\t(.*)\r\n\tLogon ID.*Object Name:\t\t(.*)\.(.*)\r\n\tHandle ID.*WriteData* |
When testing the regular expression against the contents of a typical 4663 event (the content has to point to a file, not a directory), then you should see that it extracts 3 substrings:
- Domain
- Filename (without extension)
- Extension (circled in red)
It is only the extension that will be passed to the anomaly feature to ultimately detect and alert on new extensions.
4. Setup Anomaly
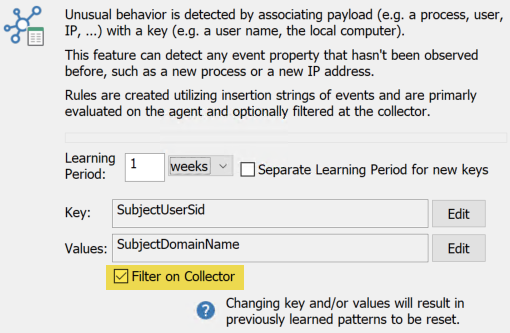
After the filter properties and the RegEx are setup, the filter can be configured to be an Anomaly filter instead of a typical Include filter. Back on the main filter dialog, click the Anomaly radio button in the Filter Settings section and click the Anomaly ... button.
In the resulting dialog, click the EDIT button in the Key section and select insertion string 1 for the key. Repeat for Values below but this time specify insertion string 3.
Explanation: Insertion string 1 will contain your domain name, a static text that should not change (on purpose). Insertion string 3 will contain just the extension of whatever file is being written.
Optional: Filter on Collector
Filtering anomalies on the collector is useful if you collect 4663 events from multiple hosts, e.g. multiple file servers and/or workstations. This ensures that an extension seen on one host won't trigger an anomaly if that same extension pops up on a different host. Without this option enabled, anomalies are processed separately on each agent and may result in multiple, identical alerts.
Then, specify a reasonable learning period (e.g. 1 week). The longer the learning period, the fewer false positives you will see for commonly used file extensions. Important: The insertion string descriptions shown in the anomaly dialog (SubjectUserSid, SubjectDomainName) can be ignored since they reflect the original insertion strings, not the ones modified via regex.
5. Configure Actions
With steps 1-4 complete, EventSentry will build a list of known file extensions during the learning period as it encounters and proceses 4663 events. Once the learning period has elapsed, any new file extension encountered will mark event id 4663 as an anomaly.
It's important to understand that an event being marked as an anomaly doesn't result in any special alert or notification, a separate filter (and possibly action) will need to be setup to act on the anomaly. The most common activity after an anomaly is detected are:
- Trigger an email (or similar alert) or a process
- Mark the event to require an acknowledgment in the web reports
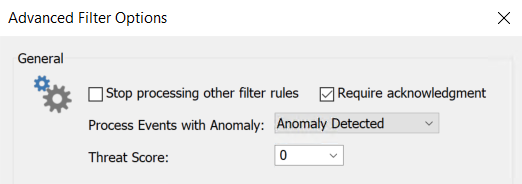
In order to process an event that is an anomaly, the advanced filter option Process Events with Anomaly can be used. For this example, the option Anomaly Detected should be used.
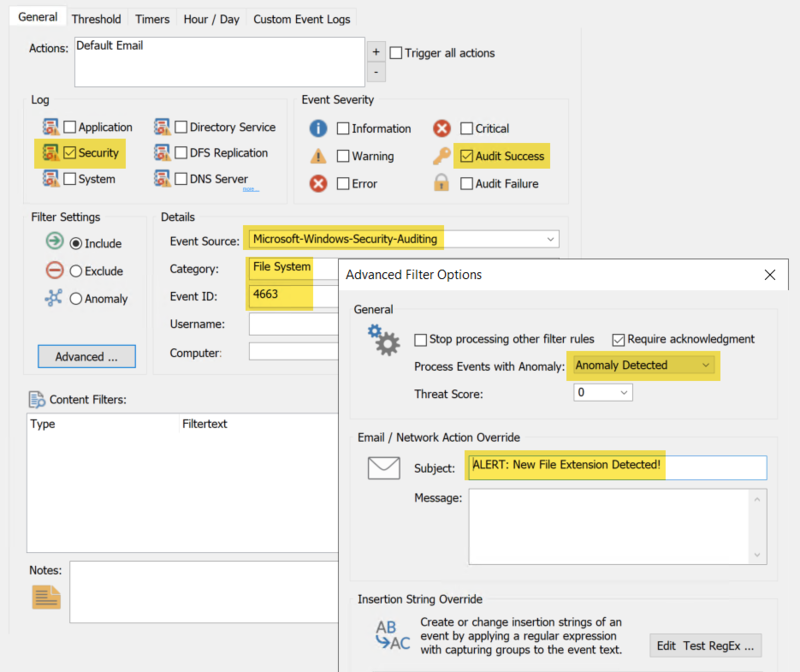
For example, to set up a filter that sends an email notification when event id 4663 with an anomaly is found, you can create a filter that matches our screenshot below. JSON syntax for this filter is available below (step 7). As in step 2a, you can copy the JSON syntax to automatically create the filter.
6. Anomaly Filter Syntax (JSON)
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 |
{
"type": 2,
"active": 1,
"name": "4663",
"uuid": "229733a8-94db-40d8-a330-4521de1b8ce6",
"version": 13,
"order": 0,
"builtin": 0,
"isfolder": 0,
"applyToCollectorSideThresholds": 0,
"requireAck": 0,
"stopProcessing": 0,
"anomalyFiltering": 0,
"threatWeight": 0,
"anomaly": {
"learningPeriodSeconds": 10800,
"learningPeriodSeparate": 0,
"keys": "1",
"values": "3"
},"overrideSmtpSubject": "RklMRSBDSEFOR0U=",
"overrideSmtpMessage": "JFNUUjINCiRTVFIzDQokRVZFTlROVU1CRVI=",
"useRegex": "LipBY2NvdW50IERvbWFpbjpcdFx0KC4qKVxyXG5cdExvZ29uIElELipPYmplY3QgTmFtZTpcdFx0KC4qKVwuKC4qKVxyXG5cdEhhbmRsZSBJRC4qV3JpdGVEYXRhKg==",
"logs": [ "SEC" ],"severities": [ "AUDITSUCCESS" ],"source": "Microsoft-Windows-Security-Auditing",
"category": "File System",
"eventid": "4663",
"chainType": 1,
"textfilters": [ { "insertionString": 0,
"comparisonType": 0,
"text": "TESTGROUND",
"type": 1
}],"threshold": {
"type": 0,
"limit": 0,
"interval": 0,
"intervalScale": 0,
"processBefore": 0,
"processAfter": 0,
"processAfterFirstOnly": 0,
"logImmediate": 0,
"logInterval": 0,
"logSeverity": 2,
"matchType": 1
},"timer": {
"enable": 0,
"interval": 0,
"intervalScale": 0
},"bootBehavior": 0
}
|
7. Notification Filter Syntax (JSON)
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 |
{
"type": 0,
"active": 1,
"name": "New File Extension",
"uuid": "9b969325-6bb0-42ca-87ee-333d64247cfb",
"version": 2,
"order": 0,
"builtin": 0,
"isfolder": 0,
"applyToCollectorSideThresholds": 0,
"requireAck": 1,
"stopProcessing": 0,
"anomalyFiltering": 1,
"threatWeight": 0,
"overrideSmtpSubject": "UFJPRCBURVNUOiBOZXcgRmlsZSBFeHRlbnNpb24gRGV0ZWN0ZWQh",
"logs": [ "SEC" ],"severities": [ "AUDITSUCCESS" ],"source": "Microsoft-Windows-Security-Auditing",
"category": "File System",
"eventid": "4663",
"chainType": 0,
"threshold": {
"type": 0,
"limit": 0,
"interval": 0,
"intervalScale": 0,
"processBefore": 0,
"processAfter": 0,
"processAfterFirstOnly": 0,
"logImmediate": 0,
"logInterval": 0,
"logSeverity": 2,
"matchType": 1
},"timer": {
"enable": 0,
"interval": 0,
"intervalScale": 0
},"bootBehavior": 0
}
|