How can I detect insider threats with EventSentry?
EventSentry has a dashboard you can import into Web Reports that is designed to help detect insider threats. To install it, first download it from this link:
Save this file to the following path on the EventSentry server:
C:\Program Files\EventSentry\WebReports\web\webapps\ROOT\WEB-INF\application\conf\
Then follow the steps in this KB article to import the Insider Threats dashboard to Web Reports: https://www.eventsentry.com/kb/494-how-do-i-import-custom-dashboards
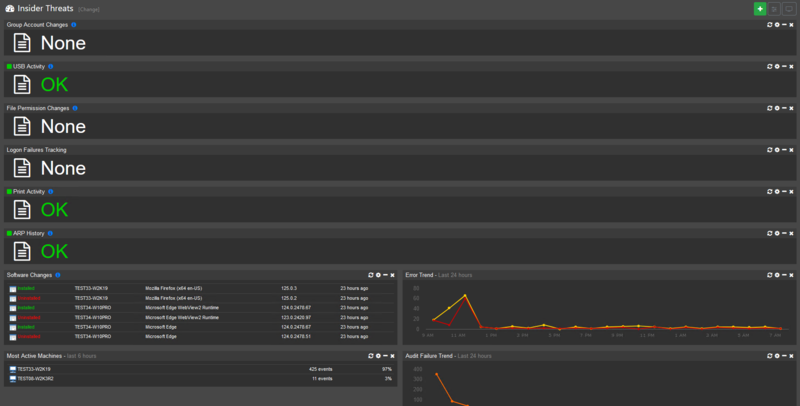
These tiles are meant to give an overview on topics that might indicate insider threats, for example showing if a group membership is changed, USB devices are attached or written to, logon failures, and more.
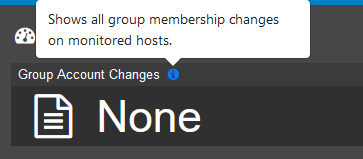
Each of the tiles on this dashboard have a blue information icon that you can hover over to see what it covers:
The tiles in the dashboard might need to be adjusted to better suit your environment. For example, it might be normal for a certain user to use USB sticks so you can exclude them from the USB Activity tile. Click the gear in the top right to adjust the tile query and remove the user.
In addition to this dashboard, EventSentry has some security-focused event log packages that can help detect insider threats. Open the EventSentry console to Packages > Update > Check Now to download the latest updates to packages.
The recommended packages are:
- Security Processes
- Security Logons
Note: these packages were previously called "Threat Detection" and "Process Activity." These old packages have the same filters as the new packages, just under a different package name.
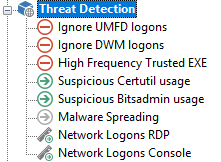
These packages monitor your event logs for events that might be threat indicators. For example, Security Processes detects if multiple admin tools are run in a quick succession or if unsigned files are launched. It can also detect if the same process is launched across the network in a short period. Security Logons can detect if a user account logs onto multiple machines in a short period via RDP or Console.
These packages also use a new feature in EventSentry 5.1: anomaly detection. For a set learning period, the agents will monitor activity such as what processes are launched on a machine and what users logon and from what IP. After this learning period is over, if a process is launched that wasn't launched before, or a user logs on that wasn't logged on before you can be sent an email.
You may need to configure these packages to fit your network as well. For example, the Security Processes package's "Malware Spreading" filter monitors if a process is launched multiple times across the network in a short period. You may know that a certain process in your network does this normally and is not an indication of a threat, causing a false positive alert. In this case, you can add the process to the "High Frequency Trusted EXE" filter to exclude it from being monitored.
Lastly, we recommend creating an event log filter that will alert you if a user logs in outside of your normal business hours: https://www.eventsentry.com/kb/511