Agent Security Options
|
Agents: only store the group agent is a member of in local registry config By default all remote agents receive the full EventSentry configuration transmitted, including all groups and hostnames contained therein. This may not be desirable in situations where the same EventSentry configuration is used to monitor disparate & isolated networks, such as in MSP environments. Enabling this option ensures that a remote agent only stores the group data from the group it is a member of. |
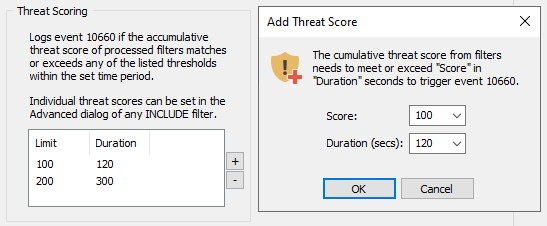
Threat scoring is an option associated with "Include"-type event log filters. Every time a filter matches an event, the configured threat score (if set) will be tracked and added to any existing threat score in a sliding-window fashion. If the accumulative threat score reaches or exceeds any of the configured limits, event id 10660 is logged - along with the content of the event log filters (up to 10 max). Multiple threat score limits can be configured. The overall threat score resets itself after the duration is elapsed.
EventSentry ships with a free Geolite city geolocation database which will supplement IP addresses with their corresponding geolocation. EventSentry includes this database, which is updated with every EventSentry version update that is released. The latest version of the database can also be downloaded from https://dev.maxmind.com/geoip/geoip2/geolite2/. Follow the steps below to update the geoip database:
1.In the management console, click on "Services"
2.Stop the "Network Services" service
3.Stop the "Collector" service if it is running
4.Replace the GeoIP database file with the latest version (mmdb format only!)
5.Start the "Collector" service again if it was running
6.Start the "Network Services" service

Utilizes three public black lists (OTX, Firehol, Blocklist.de) that are downloaded every 4 hours to identify potentially malicious IP addresses.If an API key is configured, then a black list from AbuseIPDB is downloaded (in addition to the 3 free blacklists) and a threat status of each IP address is also obtained from the AbuseIPDB web site in real time. See AbuseIPDB Pricing for more details, a free service with limited checks is available (1000 queries / day as of November 2020).
Custom Block List: In order to incorporate third-party block lists, save the blocked IPs in the following format to the file %SYSTEMROOT%\system32\eventsentry\temp\eventsentry_threatintel_custom.tmp. This file, when present, will be imported every time the other blacklists are downloaded:
IP;Confidence Score;Title
IP: IP Address
Confidence Score (optional): Number 0..100
Title (optional): Threat title or description
Example:
10.20.30.40;60;Port Scan
10.20.80.22;90;Web Attack,Port Scan,Spam
Optional fields can be omitted: "Confidence Score" defaults to 50 if not present, "Title" is set to "n/a" if not present. At minimum, one IP address per line must be specified.
The threat intelligence status can be used in event log filters and in the web reports to filter reports based on the threat status of an IP address.
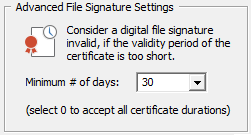
Additional FileSignature Settings
Certificates are used by software developers to digitally sign binary files like executables. Certificates usually have a validity period that ranges between 1 and 3 years. Some online services allow software authors to sign files with certificates that are only valid for a very short time (e.g. 3 days), without the users having to undergo the usual extensive security checks. Consequently, files signed with such certificates should undergo extra scrutiny and can be considered "unsigned" in EventSentry by setting a minimum certificate validity period. For example, if the Minimum # of days setting is set to 30, then a file signed by a certificate that was only valid for 14 days will be considered unsigned by EventSentry, as if the file has no digital signature at all.
This setting only affects files with embedded digital signatures, files implicitly signed via catalog files (e.g. files that are part of Windows) are exempt from this enhanced verification.