The System Administrator! AKA the Sysadmin. The keeper of the network, computers – well basically all things technology. The one who is hated for imposing complex passwords and other restrictions, but taken for granted when everything works well.
They are the first to be called when “facebuuk.com” reports: “domain does not exist”. They are the first to be contacted in the early hours of the morning with a “I can’t print” complaint – without ever receiving a cordial “Good morning, how are you?” greeting. They are the ones who are expected to fix a personal laptop, with the promise of some donuts that never arrive.
If you are a Sysadmin, then I’m sure you’ve been there. While Diana at the reception desk keeps calling you when she can’t listen to her favorite radio because the page won’t load, but never opening a ticket. Then you are reading that this January’s Patch Tuesday has about 98 CVEs, 10 of which are considered critical.
In the list of CVEs, you recognize the usual actors: NTLM, ODBC Driver, RPC, Print Spooler, Microsoft Office, Microsoft Exchange Server, etc. You think, “When are they going to fix everything for good?”
You need to be everywhere at the same time – add paper to Carla’s printer on the second floor, who was hysterical because she couldn’t print.
Alas, it’s too late to go back and choose another career. You have made up your mind, you are going to be the best Sysadmin you can be. Some days you have slight concerns about your mental health, but you roll up your sleeves and keep going – one coffee at a time.
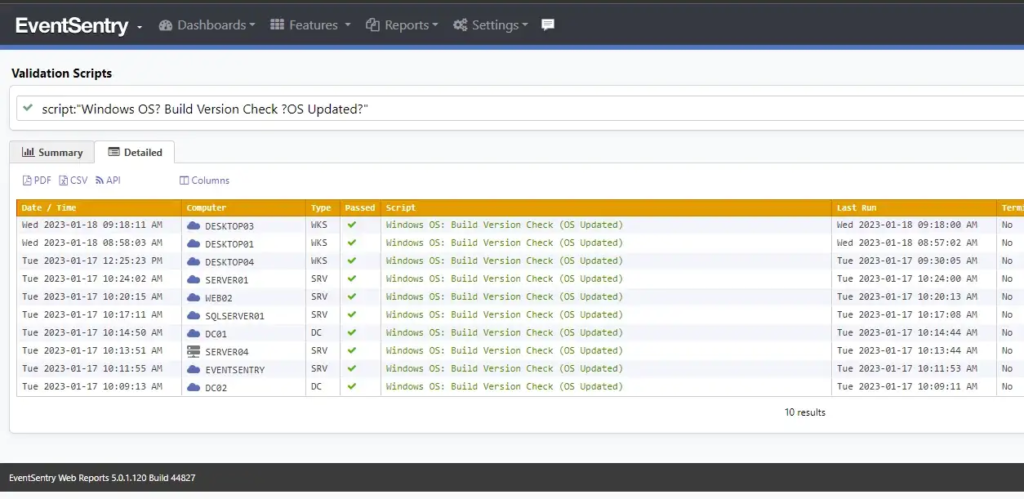
Unfortunately, there is no software to make Carla read the printer error message before calling you. But with EventSentry, you can check if the Patch Tuesday patches have been applied – even if you don’t use WSUS (or especially when you use it). For example, with validation scripts you can quickly see if any machines on the network are not running the latest build (patch) of Windows:
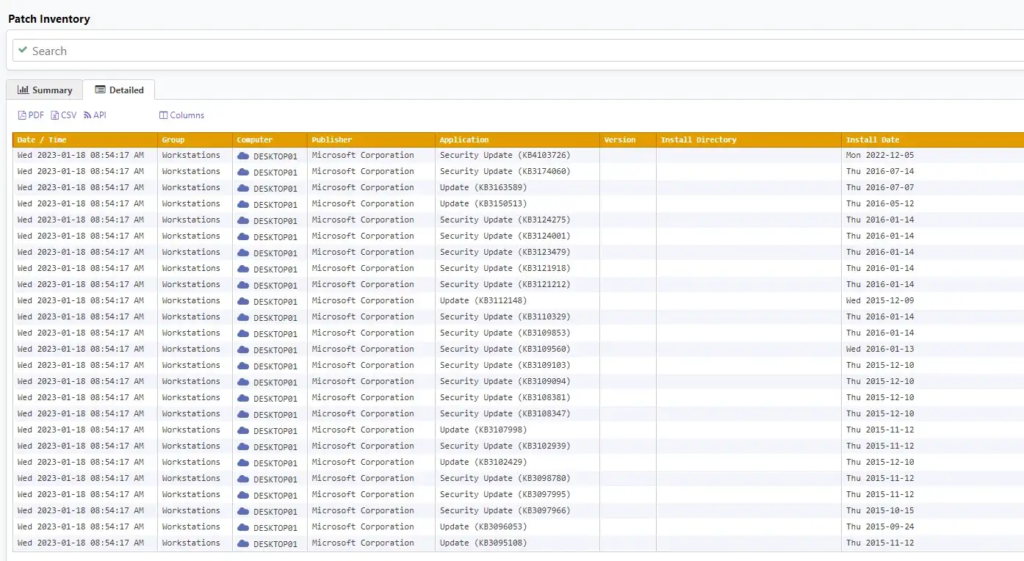
Or, you can verify whether a specific patch has been applied:
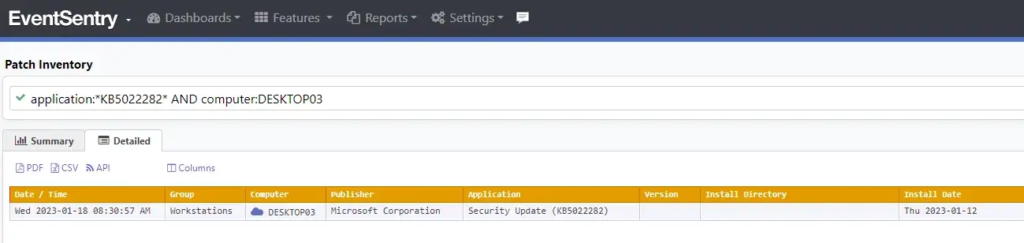
And you can also search if the patch for CVE-2023-21674 (KB5022282) (Windows Advanced Local Procedure Call (ALPC) Elevation of Privilege Vulnerability) was applied on the CEO’s computer:
But you’re not restricted to Windows patches, you can also check if any software on any of the computers is out of date:

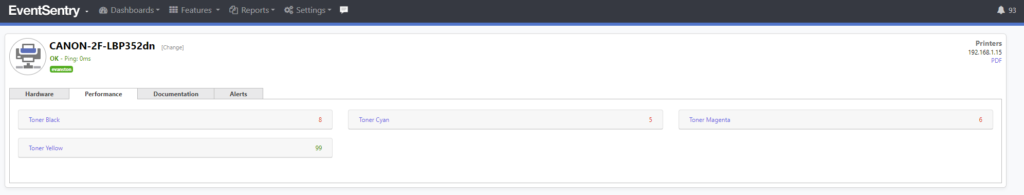
And of course, you can also check if Carla’s printer is out of paper or toner – before making the trip upstairs to her office:
And best of all, everything posted here is included & enabled by default with EventSentry. No need to spend hours configuring or activating options. Simply install EventSentry and you will have access to all of this – out of the box!
In the career of a Sysadmin, there are many day-to-day things that you can’t control. That’s why we created EventSentry, so that you can have control over the network, the devices and, most importantly, the patches. Which of course, leaves you more time to fix Diana’s internet radio!