Even though disk storage is cheaper and faster than ever, for some reason I still run into disk space problems on occasion. The most common disk space problems I run into is a full C drive (why would you need more than 4Gb for the OS?) or a database that grows too large.
We have found and utilized several tools over the past years and I am going to share some of my approaches to quickly identify space hogs, free up disk space and deal with fragmentation.
Once a machine is low on disk space one will usually want to find out which files use up the most space and move them to a new volume or send them to data heaven for good. There are a lot of tools out there that visualize disk space consumption on a volume, but my favorite by far is Windirstat. Windirstat uses a treemap which displays every file in a colored rectangle and was inspired by KDirStat from Linux (the original author really wants to make sure you know what the original is). The size of the rectangle is proportional to the file size, so you will either want to look for clusters of many small files (e.g. to spot lots of unneeded temp files) or for large rectangles to identify any files you might not need anymore. I find it incredibly easy to spot files that can be safely deleted with Windirstat. The screenshot below shows what Windirstat looks like on my Vista laptop with a 64Gb HD.
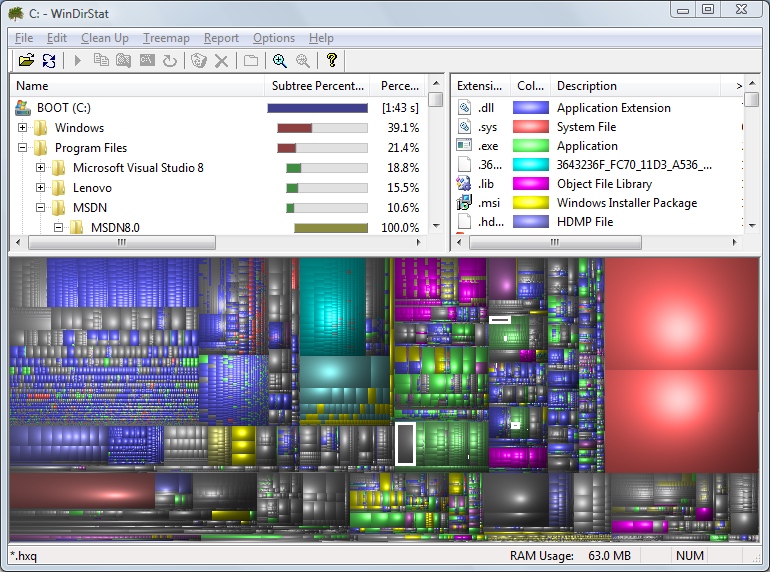 Of course, just running Windirstat alone doesn’t mean that you will be able to find files that can be safely deleted. But once you have identified files that do occupy significant amounts of disk space, you can engage in research to determine whether these files can be compressed, moved or deleted. Usual candidates are the temporary files, pagefile, IIS log files, NTBackup temp files and temporary installer MSI files (more on that below).
Of course, just running Windirstat alone doesn’t mean that you will be able to find files that can be safely deleted. But once you have identified files that do occupy significant amounts of disk space, you can engage in research to determine whether these files can be compressed, moved or deleted. Usual candidates are the temporary files, pagefile, IIS log files, NTBackup temp files and temporary installer MSI files (more on that below).
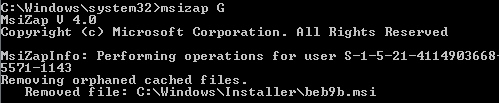
Windows will sometimes cache and leave installer files on your C drive, even when the application is no longer installed or has been upgraded. Depending on how long ago the OS was installed, this can be between a few hundred megabytes or nothing at all. You can delete those so-called “orphaned cached Windows Installer data files” with the msizap.exe utility, using the G command-line switch. Using msizap has been the last resort for me a few times, freeing up significant space on the C drive of servers when nothing else could be moved or deleted. Msizap is part of the Windows Installer 4.5 SDK which can be downloaded from http://www.microsoft.com/downloads/details.aspx?FamilyId=6A35AC14-2626-4846-BB51-DDCE49D6FFB6&displaylang=en. The screenshot below shows msizap in action.
 Now, after cleaning up all the space we’d want to defragment our drive as well, right? Disk defragmentation software has been around since MS-DOS, but people are still debating whether defragmentation software, especially commercial one, is worth the effort. It is sort of like taking multivitamins – it most likely doesn’t hurt but there is no clear indicator that it cures diseases or makes you feel better after taking them.
Now, after cleaning up all the space we’d want to defragment our drive as well, right? Disk defragmentation software has been around since MS-DOS, but people are still debating whether defragmentation software, especially commercial one, is worth the effort. It is sort of like taking multivitamins – it most likely doesn’t hurt but there is no clear indicator that it cures diseases or makes you feel better after taking them.
 Some operating systems, most notably Linux and Mac OS X attempt to prevent fragmentation as much as possible and don’t even include defragmentation software, but the Windows software market is awash with both free and commercial defrag software. If you are interested in learning more about fragmentation and its cause, then Wikipedia has an article about defragmentation.
Some operating systems, most notably Linux and Mac OS X attempt to prevent fragmentation as much as possible and don’t even include defragmentation software, but the Windows software market is awash with both free and commercial defrag software. If you are interested in learning more about fragmentation and its cause, then Wikipedia has an article about defragmentation.
So is it worth it to use or invest in commercial defragmentation software? I think it depends. I have used various defragmentation programs over the last 10 years or so, and have seen one case where a MSSQL database on an extremely badly fragmented partition had became so slow that it was essentially unusable (yes, the database was for EventSentry 🙂 ). Defragging this partition with PerfectDisk solved the problem and the database was performing well after defragmentation. So yes, fragmentation can be bad if it gets out of control, though this is the only time I remember a defragmentation having such a significant impact. If you have a partition with little disk space available and lot write activity, then it will probably make sense to continuously defrag the partition to ensure optimal performance. Otherwise I think it is a luxury and will not yield significant disk performance benefits.
You can also use the -a switch of the defrag.exe utility that ships with Windows to analyze a drive and get basic metrics as to whether the drive should be defragmented or not. However, if you have a lot of machines then running defrag.exe on all of them manually can be tedious, especially since you would need to do that on a regular basis (e.g. monthly). Fortunately, you can use EventSentry‘s application scheduler feature to automate this task in three simple steps (in this example we will focus only on the system drive). Since the application scheduler logs output from any command-line utility you run to the event log, we can actually get an email when Windows thinks that a drive is fragmented.
- Create an embedded script (e.g. DefragCheck.cmd) that runs “defrag.exe %Systemdrive% -a -v“
- Create a system health package and add a new application scheduler object to it – making sure that both check boxes in regards to error levels are checked. Pick the embedded script @DefragCheck.cmd and schedule it to run. Everytime defrag.exe is executed, EventSentry will log an event to the event log with the output of defrag.exe.
- Create a new event log package and add a filter that matches the events generated (Log=Application, Source=EventSentry, EventID=10200) and additionally looks for the string *You should defragment this volume*.
Voila – now you will get an email every time defrag.exe determines that a drive is fragmented – and only if it’s fragmented.
Defrag.exe is of course only one of the many utilities out there that can determine fragmentation, and you will likely get different results from different utilities. For example, it’s very likely that defrag.exe tells you that a drive is not fragmented, when a different software (e.g. PerfectDisk) will tell you otherwise.
One scenario where you definitely do NOT want to use defragmentation software is on SSD drives, as they usually don’t suffer from the same random access delays and defragging will reduce the lifespan of the drive.
Best,
Ingmar.