There has been a lot of concern and uproar recently about the .NET Framework Assistant Firefox Add-On (plug-in), that Microsoft silently installs with the Microsoft .NET Framework 3.5 Service Pack 1 (which was pushed in early 2009 with Windows Update). As such, if you are using Firefox, then there this is a very high probability that you have this Firefox Add-On installed, maybe even without knowing it.
To quote Microsoft: “In the .NET Framework 3.5 SP1, the .NET Framework Assistant enables
Firefox to use the ClickOnce technology that is included in the .NET
Framework.”
There are dozens of blogs that complain about the security implications, how the Add-On cannot be uninstalled and eventually post instructions on how to remove the Add-On from your computer, essentially implying that the AddOn harbors major security risks. Contrary to most Firefox Add-Ons, this one can’t be uninstalled through the browser since it was installed at the “computer level”. As such, you have to remove files from the file system and modify the Firefox configuration to disable it.
I’d have to admit that I haven’t heard much about the ClickOnce technology before this sneaky little AddOn was set free, and the buzz words one reads in all the blogs, newspapers etc. certainly have the potential to make one uneasy and follow the surgical removal procedure without much hesitation:
- Microsoft installs .NET AddOn without user approval!
- AddOn can’t be uninstalled
- AddOn silently runs .NET applications without user knowledge!
- ActiveX security hell is back!
So is the AddOn a security risk and do you have scramble to rip it out? Not in my opinion, and I will explain why.
 In this post I will clear up some misconceptions about the ClickOnce technology, but also show you how to remove the AddOn from any number of computers with a few clicks – using our new AutoAdministrator 2.0 – just in case you do want to rip it out :-).
In this post I will clear up some misconceptions about the ClickOnce technology, but also show you how to remove the AddOn from any number of computers with a few clicks – using our new AutoAdministrator 2.0 – just in case you do want to rip it out :-).
What most people don’t know, is that the ClickOnce “technology” is already present in Internet Explorer, and is not even close to what was/is possible with ActiveX applets.
ClickOnce applications run in a sandbox, similar to Java, and – by default – do not have any permission outside the sandbox. As such, a web site can’t just install a trojan horse or spam client on your computer – at least not using ClickOnce. The users permission is asked before elevated permissions are assigned to the application, and software that’s being installed can be signed – just like Windows applications are. Please see the Microsoft article below for more information on ClickOnce deployment and security:
ClickOnce Deployment and Security
So the AddOn is really just a gateway into something that is already on your system in the first place – .NET. Java does the same thing, and the AddOn Microsoft provides is likely much leaner than the Java plugins – and doesn’t register a new plugin with every new Java update that is released.
Don’t get me wrong – Microsoft could have handled this much better, and the inability to uninstall the AddOn really doesn’t help their case.
Oh, and by the way, to see a sample ClickOnce application then you can click here. It’s hosted by the author of the FFClickOnce Firefox AddOn, a predecessor of the .NET Framework Assistant if you will.
However, Microsoft has recently provided information on their site that outlines the required steps to remove the Add-In from Firefox, and has also released an update that will allow you to uninstall it on a per-user basis. Keep in mind that even with this update, every user would have to uninstall the Add-On manually:
Update to .NET Framework 3.5 SP1 for the .NET Framework Assistant 1.0 for Firefox
Having said all that, you might still want or have to remove the AddOn from multiple computers if you need to remove the ability for your users to run ClickOnce applications from Firefox. The good news is that you can remove all files as well as all registry entries that are associated with this Add-On from any number of computers within a matter of minutes — using AutoAdministrator.
AutoAdministrator integrates with ActiveDirectory, and lets you query/modify files, services, registry entries and more on any number of computers with the click of a few buttons. Read on to find out more.
Microsoft states that you need to perform three steps to remove the Add-On (official removal instructions – KB963707):
1. Delete the registry key HKEY_LOCAL_MACHINE\SOFTWARE\Mozilla\Firefox\Extensions\{20a82645-c095-46ed-80e3-08825760534b}
2. In the Firefox preferences (about:config), right-click the general.useragent.extra.microsoftdotnet property and select “reset”.
3. Delete the folder %SYSTEMDRIVE%\Windows\Microsoft.NET\Framework\v3.5\Windows Presentation Foundation\DotNetAssistantExtension\DotNetAssistantExtension.
We can accomplish (1) and (3) with AutoAdministrator, which does remove the Add-On. It doesn’t reset the setting inside Firefox (2), but that should be merely a formality without the actual plug in. Our tests have shown that the plug in is gone after deleting the registry key and the directory on the file system.
There are two prerequisites for this to work: Your remote machines need to have the remote registry service running (you can temporary toggle that too with AutoAdministrator if it’s not running!) and the ADMIN$ share needs to exist.
As with all things you can do with AutoAdministrator, you should be very careful. We cannot take any responsibilities if you end up corrupting your Firefox installations, or worse, the Windows OS.
So, fire up AutoAdministrator and select the computers you want to uninstall the pesky Add-On from in the right pane. Then, select “Registry” from the toolbar and paste the key from step one in there and select “Delete key”.
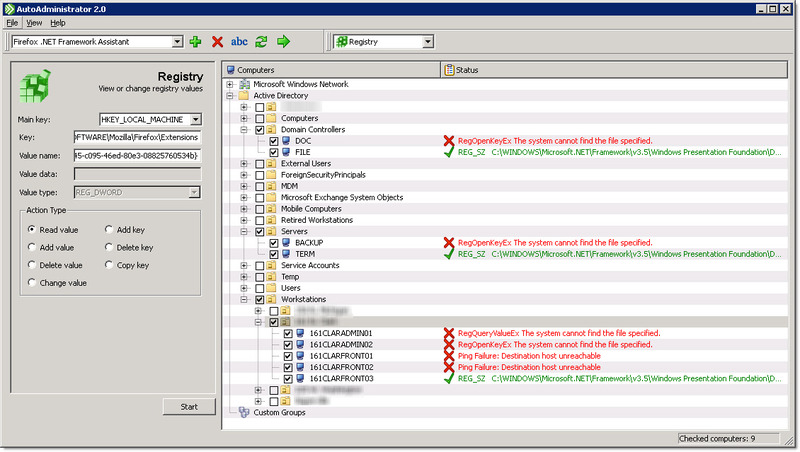 The screen shot above shows the result list, using the “Read Value” option. To actually delete the key, you would need to select “Delete key”. Machines that are turned off are displayed as “Ping Failure: …”, and machines that don’t have the Add-On installed show a Windows API error message.
The screen shot above shows the result list, using the “Read Value” option. To actually delete the key, you would need to select “Delete key”. Machines that are turned off are displayed as “Ping Failure: …”, and machines that don’t have the Add-On installed show a Windows API error message.
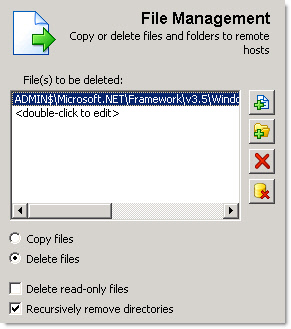
When you are doing ripping the registry settings out, you can delete the folder as well. This time, select “File Management” from the toolbar, and paste the directory in there. Note that the remote path should start with ADMIN$, as shown in the screen shot below:
 You can also save these s
You can also save these s
ettings as a preset, so that you can retrieve these settings at any point in the future with the click of a button.
I hope this information helps you make an informed decision as to how to proceed with the AddOn if it’s already installed in your network. You can
- Leave it
- Give your users instructions on how to disable it
- Roll-out the Microsoft patch to give your users the ability to uninstall it ( arguably identical to (2) )
- Remove it from all systems with AutoAdministrator or scripts
I think if this exercise reveals anything, then it’s that Firefox’s AddOn framework leaves some room for improvement. For example, why did Firefox not inform me that this AddOn had been installed? Skype also silently installs an AddOn, though that can be removed easily.
And if you’re really serious about browser security, then you might want to check out the Flashblock AddOn. It disables all flash animations by default, leaving placeholders that you can click to load any flash animation. This improves page load times, can help suppress annoying flash-based ads and of course helps security. I haven’t tested it on many sites yet, but it can quickly get annoying if you’re accessing a lot of web sites that contain reporting widgets that are flash-based.
So long,
Ingmar.