Now that EventSentry v2.91 has been released, I’m happy to have the opportunity to blog about our monitoring solution again.
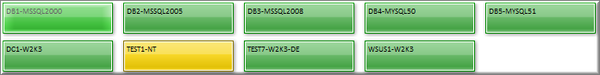
The most significant new feature in EventSentry is the Health Matrix, a new way to see your network status in a space-efficient way. In fact, you can see the overall health status of your entire network on a single screen, even if it consists of hundreds of hosts.
We also made numerous other changes throughout the web reports, and added some exciting new filtering capabilities with our event log filters, as well as improved speed with the event log engine and file checksum generations.
EventSentry v2.91 also includes many minor improvements throughout the application, including service monitoring, process tracking and more. We have also updated EventSentry Light, and a new version will be released in the coming days after we have completed testing.
But now to the new features in version 2.91:
Health Matrix
In the health matrix, each host is displayed as a colored square, circle or rectangle, with the color indicating the overall health of the monitored computer. When all of the monitored components of a host are in an OK status, the color of the square is green. The color will change to orange or red when a problem is detected, depending on the number or severity of the issue.
 The health matrix is highly customizable, for example both the size and shape of the icons can be adjusted depending on the size of the network (and your monitor).
The health matrix is highly customizable, for example both the size and shape of the icons can be adjusted depending on the size of the network (and your monitor).
 Event Log Monitoring
Event Log Monitoring
In 2.91, the event log filtering engine was improved, resulting in reduced CPU usage of the event log monitoring component. Since the CPU usage of the EventSentry agent is already quite low, you will most likely only notice this improvement on hosts that generate an extremely large number of events, such as domain controllers.
Also new is the ability to filter events based on insertion strings in addition to just filtering based on the event message text. This means that one can now match individual strings inside event messages against strings, numbers, file checksums and group memberships. If you are not familiar with the term “insertion string”, then I highly recommend my previous post about event message files before you read on.
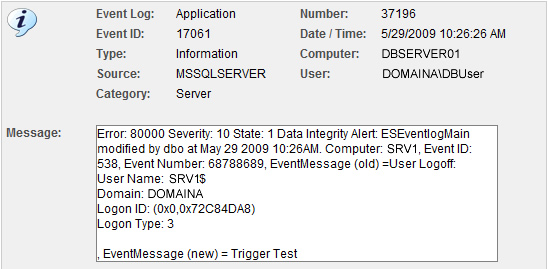
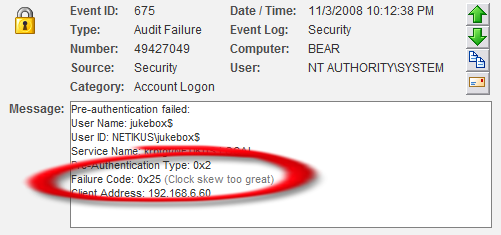
Consider the following hypothetical example: The environment-monitoring component of EventSentry logs event id 10908:
The temperature (78.21 degrees F) has fallen outside the configured range (60F to 76F).
which is defined as:
The temperature (%3 degrees %4) has fallen outside the configured range (%1%4 to %2%4).
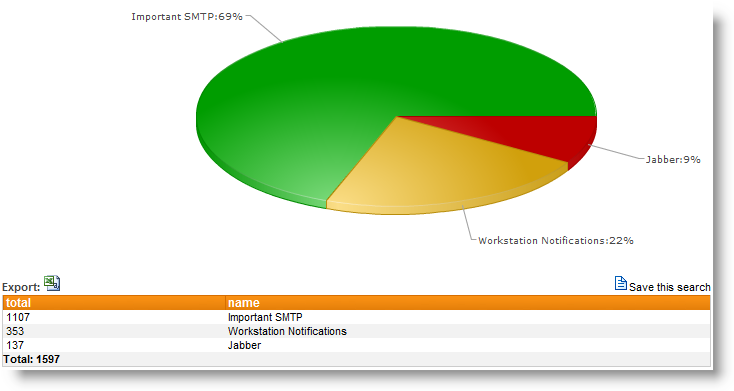
This event obviously informs us, that the current temperature has exceeded a set limit. Now let’s say that we wanted to get an email when the temperature exceeds the limit, but also send a page when the temperature exceeds 90 degrees.
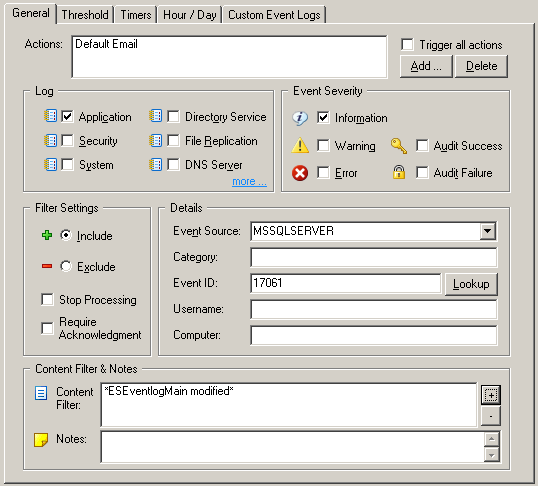
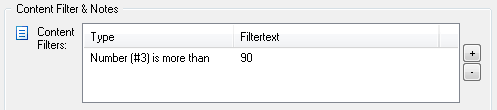
The new filtering feature allows you to do just that, by using the numerical comparison functionality with insertion strings (of course you would also need to set the hour/day properties). Assuming that you already have a filter in place for regular email notifications, you would simply setup an additional include filter that would evaluate insertion string 3 (%3) and only match if the number is above 90. See the screen shot below for the example. The result is a filter that only matches when then the temperature exceeds 90 degrees.
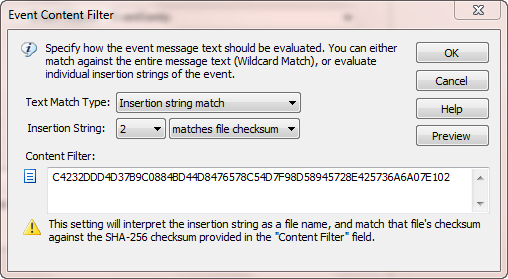
 2.91 also includes two more comparison options, file checksums and group membership. So, if an insertion string represents a filename (e.g. from a security event), then EventSentry can create a SHA checksum from the specified file and compare it with the value that you specified. Another example would be a security event that includes a username in an insertion string, in which case you could setup a filter that would only match if that user is a member of particular group you specify. Both examples are mostly applicable for security events, since those are most likely to contain either filenames or usernames.
2.91 also includes two more comparison options, file checksums and group membership. So, if an insertion string represents a filename (e.g. from a security event), then EventSentry can create a SHA checksum from the specified file and compare it with the value that you specified. Another example would be a security event that includes a username in an insertion string, in which case you could setup a filter that would only match if that user is a member of particular group you specify. Both examples are mostly applicable for security events, since those are most likely to contain either filenames or usernames.
Using file checksums, you can be notified whenever a user plays solitaire, even when the user renames the executable.
 Simply create a checksum of the file first using shachecksum.exe (included in the free NTToolkit, make sure you account for different OS versions and platforms) and intercept the corresponding 4688 event.
Simply create a checksum of the file first using shachecksum.exe (included in the free NTToolkit, make sure you account for different OS versions and platforms) and intercept the corresponding 4688 event.
Service Monitoring
Service Monitoring now collects the username as well as the executable of a service. These additional properties are available in the web reports and in events generated, for example when the username of a service changes.
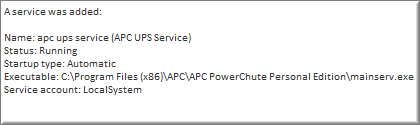 Software Monitoring
Software Monitoring
Software monitoring has been overhauled in 2.91, and some limitations and bugs have been removed. On Vista, Win2k8 and later, Windows patches are now monitored and included in the software inventory. 64-bit software is now classified as such and searchable, and searching for installed Windows Updated patches has also been simplified.
SNMP Traps
EventSentry can now send version 2c and version 3 traps, previously only version 1 traps were sent by the agent. The SNMP trap daemon was originally set to be released as part of 2.91, but this feature has been pushed back to v2.92.
Web Reporting
We have made a number of improvements in the web reporting to make using our web-based interface easier:
• Reports are now easily accessible from every page, in addition to the reports p
age.
• The database usage page now shows the actual page name in addition to the table name.
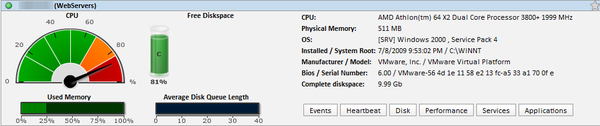
• The dashboard page has been overhauled
• The network status page can be customized (performance counters & disks)
 Miscellaneous Improvements
Miscellaneous Improvements
There have of course been other improvements across the board, such as:
• Notes can now be applied to computers
• AD-linked groups can be sorted, and authentication properties can be set globally
• Hardware monitoring now includes the IP address of an interface
• Process tracking can capture the command line of a process
• Logon tracking includes group information
• File checksum generation has been optimized and will now use fewer CPU resources (affects file monitoring and file access tracking)
• The minimum database interval for environment monitoring has been reduced to 5 minutes from 15 minutes
• Software uninstallation events now include the same information as software installation events
If you have an active maintenance agreement, then this 2.91 release will of course be free of charge. If you are not already using EventSentry, then you can download a free 30-day evaluation version from https://www.eventsentry.com/downloads_downloadtrial.php.
Happy Holidays,
Ingmar.