After launching version 2.90 of EventSentry just a few months ago, we’re excited to announce yet another major software release coming from NETIKUS.NET ltd – AutoAdministrator v2.0.
The last update of the 1.x series was released more than four years ago, so we decided to completely re-build it from scratch and add all the features that have been requested by our users since the last release. The result is a powerful tool that makes it unbelievably easy to apply changes to remote workstations and servers. Whether a change or query needs to be applied to one or 100 computers makes little difference with AutoAdministrator.
In a nutshell, AutoAdministrator lets you query or update a variety of Windows settings and services across any number of servers and/or workstations, without the need to create a script or perform the actions manually. Simply select the feature, computers (it integrates with Active Directory) and click start.
Let’s say, for example, that you needed to obtain or set the value of a registry entry across 30 machines. By just using regedit, it would probably take you a total of 15 minutes to connect, retrieve the value, and paste it to an editor/spreadsheet and move on to the next machine. The same task, using AutoAdministrator, could be done in as little as 1 minute.
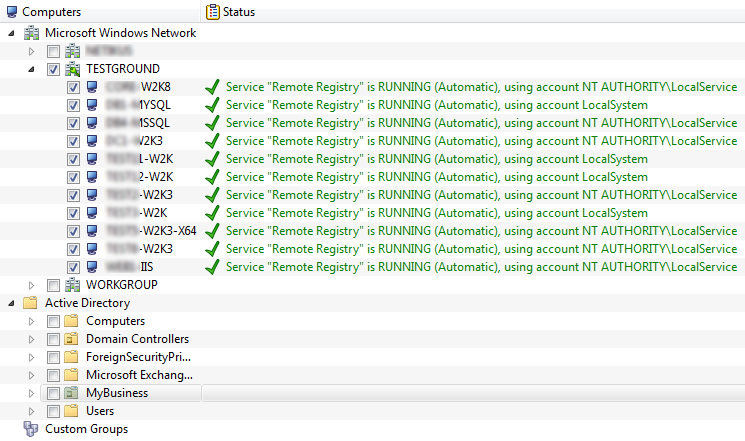
This is just one example of course, as AutoAdministrator can control services, read/set registry values, query file information, copy/delete files, manage passwords, shutdown/reboot, query logged on users, ping hosts and manage ODBC connections.
As previously mentioned, AutoAdministrator integrates with ActiveDirectory, making it a breeze to manage computers that are part of a Windows domain. You can also pull computers from the Microsoft Windows Network or create custom groups to organize computers inside AutoAdministrator. If you need to connect to remote computers using alternate (administrative) credentials, then you can assign those credentials to any Active Directory OU, group or individual computer item.
The update process itself is fully threaded, making it possible to push updates in a very short time, even to a large amount of computers.
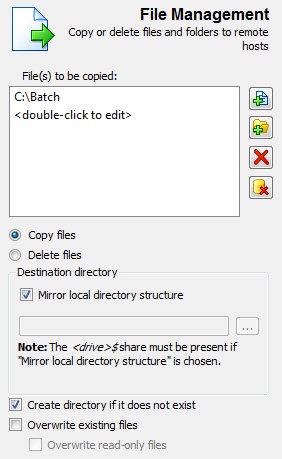
C:\Batch directory to remote computers
Another new feature is the ability to create presets, making it a snap to repeat common tasks. Simply configure the feature (e.g. query service W3SVC), select the computers and save it as a preset. The next time you open AutoAdministrator, you can simply select the preset and click “Update”.
We think that AutoAdministrator is an incredible time-saver for anybody who manages more than 10 computers, whether they are servers or workstations.
Here is a complete list of all features in the new AutoAdministrator:
Ping
Ping computers to retrieve ping statistics.
ODBC
Query, copy or delete System DSNs on remote hosts.
Passwords
Verify, update or reset passwords of user accounts on remote hosts.
Shutdown / Reboot
Shutdown, reboot or cancel a pending shutdown on remote hosts. You can optionally send a message as well.
Services
- Control any service (Query, start, stop, continue, pause, restart)
- Change startup type (manual, automatic, disabled)
- Remove service
- Change Logon (service can be automatically restarted as well)
Registry
- Values: Read, add, delete and change
- Keys: Add, delete
- Copy entire keys to remote computers
File Management
- Copy files and folders to remote computers
- Delete files and folders from remote computers
- Mirror local directories to remote computers
File Information
- Query remote files to retrieve its hash, size, attributes, modification time, version, company or description
- Remote files can be compared against a hash you provide
Logons
- Show users that are currently logged on interactively to a computer
- Count the number of users that are logged on (useful for terminal servers)
The scheduled release date for AutoAdministrator is January 12th 2009, and you can request a trial then at https://www.netikus.net/products_trial_request.html. If you can’t wait and would like to download the beta, then simply contact our support team at https://www.netikus.net/about_contact.html.
Happy New Year,
Ingmar.